The Lower Saxony police are currently receiving numerous forwardings of their spam messages from citizens who have received subsequent emails in the name of 1&1 or IONOS. The perpetrators use a pretext to ask the people they write to to click on a link or attachment, which then phishes off access data to 1&1 / IONOS!
“The password for your email address (…de) expires in 24 hours…” or
“We are updating the Terms and Conditions…”
This is what the first lines of the fake emails look like. The perpetrators hope that the people addressed will click on the links contained or even open the HTML file sent in the browser.
Two examples of fake 1&1 / Ionos emails (other variants possible):


Anyone who follows the request will be presented with a login page that is based on the login from 1&1 / IONOS.

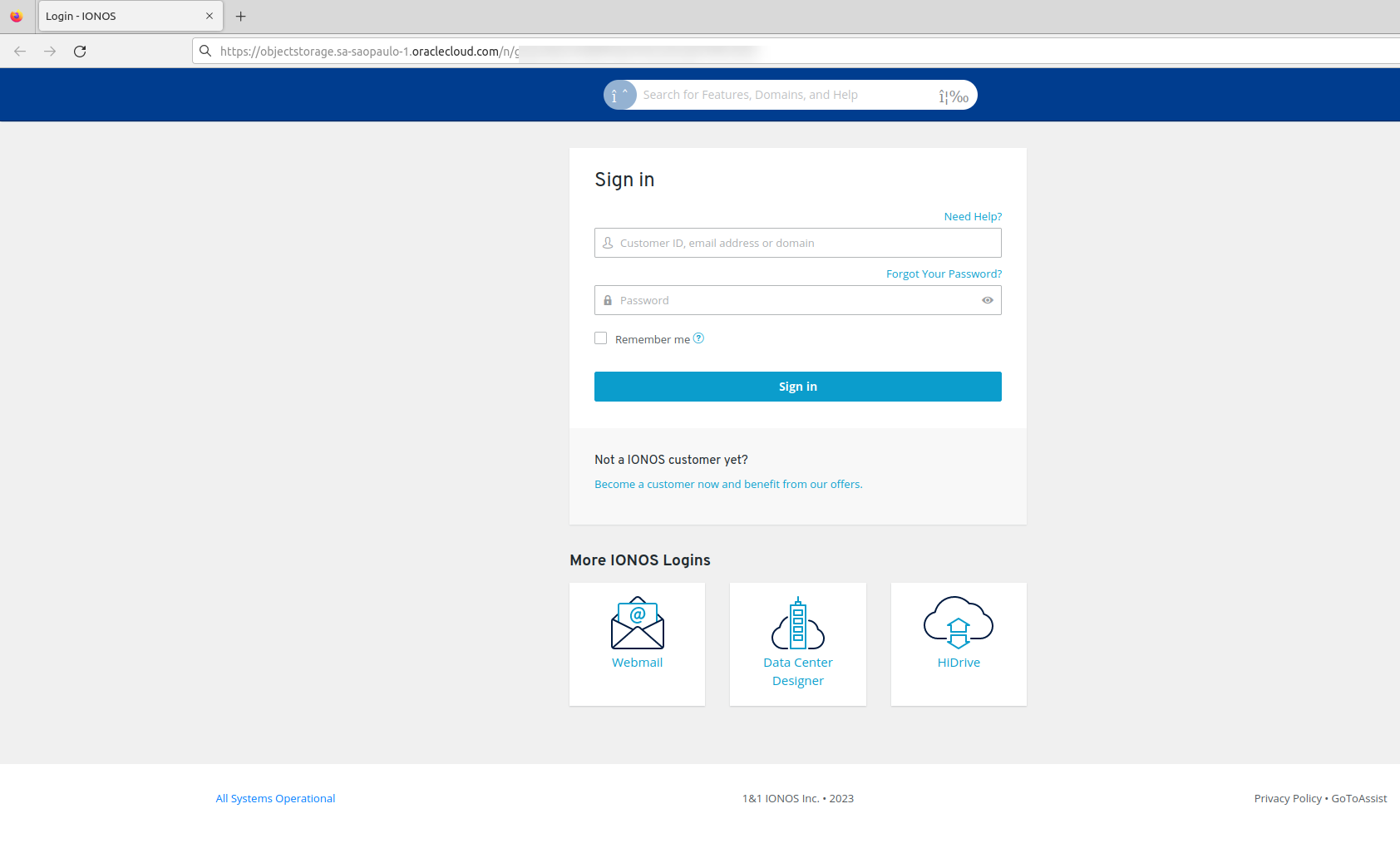
Here the perpetrators immediately access the access data to the customer portal . In the online version, this data is checked at the same time and an error message is displayed if the data was entered incorrectly.
Interestingly, in the emails we have checked so far, only 1&1 or IONOS customers were actually addressed. We currently do not know how the perpetrators obtained this data. The greeting in the email was usually “Hello” and the following email address. However, a direct customer name, i.e. a personal approach, has not yet taken place. No customer-typical data (e.g. contract numbers, customer numbers, etc.) was mentioned. We cannot check whether the contract number given in the sample email (see above) is correct.
Contact customer support!
Anyone who has fallen for this scam should immediately contact real customer support and change their own access data. Also think about passwords and access data for any existing websites, FTP access, email accounts, etc.
Check whether changes have already been made to the data (unknown email addresses, new email addresses, redirects, etc.).
Then file a report with your local police or use your respective online watchdog .
Also a note again: Do not respond to such emails without thinking and without checking . Do not click on links or attachments. You can check such claims with real customer support! In addition to the risk of phishing, there is also always the risk of malware being transferred to the websites or being executed using an attached file!
Source:
Police prevention
Current phishing warnings: HERE
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )

