The following email contains a process that is technically rarely used, but which bypasses the warning systems of browsers or protection software: the fraudulent forms are not on a fake or hijacked website, but are attached to the email as a .html attachment.
Otherwise, there is little to distinguish this email from its many fraudulent counterparts: it claims to come from Amazon and asks the recipient to fill in data in form fields for some flimsy reason. In this case, “legal provisions” are cited as the reason.
The content of this email in barrier-free plain text:
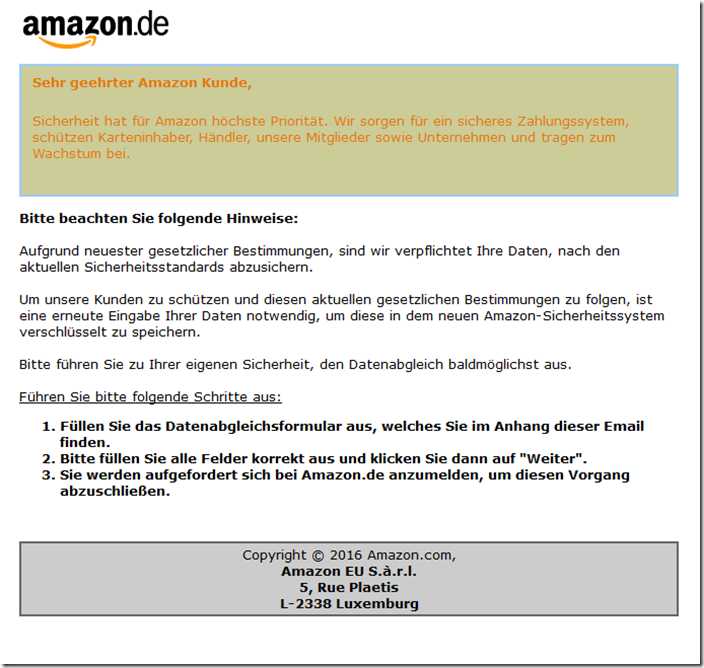
Dear Amazon customer,
Safety is Amazon's top priority. We ensure a secure payment system, protect cardholders, merchants, our members and companies and contribute to growth.
Please note the following information:
Due to the latest legal regulations, we are obliged to secure your data in accordance with the current security standards.
In order to protect our customers and follow these current legal regulations, it is necessary to re-enter your data in order to store it encrypted in the new Amazon security system.
For your own safety, please carry out the data comparison as soon as possible.
Please carry out the following steps:
- Fill out the data comparison form, which you will find attached to this email.
- Please fill out all fields correctly and then click “Next”.
- You will be asked to log in to Amazon.de to complete this process.
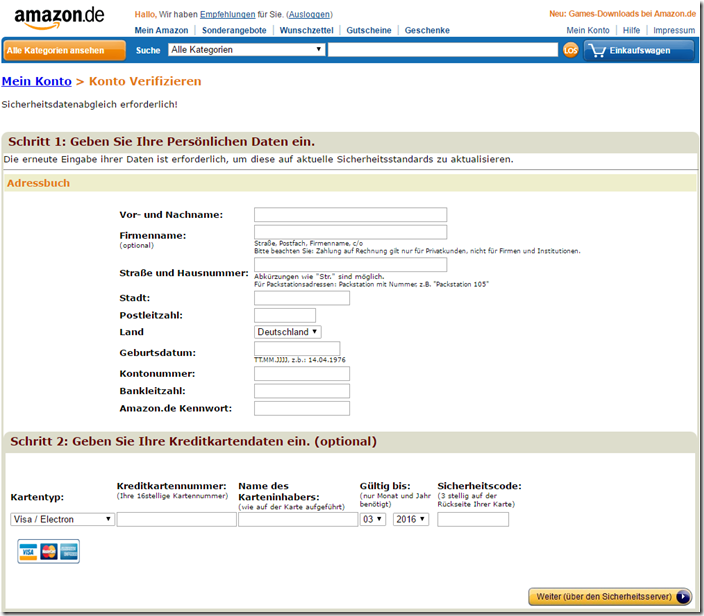
The last three points listed are relevant to the fraud process. If you open the attachment as shown, a page appears that is packed with form fields. And this is where the disadvantage of choosing this type of fraud process becomes apparent: you can't just click from page to page and display the forms step by step.
There is only this one file, only this one attempt. And all the usual query fields are there, which creates a confusing picture.
To describe the process until its end: the data entered in this form will be sent to the address “ amaz.datenschutz-verification.com ”. This is not Amazon! At the same time, the visitor is directed to the real Amazon login, so the completion of this fraud process appears completely inconspicuous and secure.
General phishing warning:
- Phishing emails generally try to appear as if they come from the relevant company . Fraudsters use these to try to get personal data, preferably bank credit cards or other payment data.
- Protection software is helpful! With updated databases and appropriate heuristics, malicious sites are often blocked. We use Kaspersky protection software .
- The real “art” of these emails is the story with which the recipient is supposed to trust the email and open the inserted link. Expression, grammar and spelling, as well as plausibility and individuality play a very important role here. Especially in the recent past, there have been an increasing number of emails that shined with individuality: they could address the recipient with the correct name and also provide actual address and personal data.
- However, you can generally note: Banks, payment and purchase portals never ask you to log in to the account using a built-in link! In addition, although a generic salutation is always an indication of phishing, an existing correct salutation is not proof of the authenticity of an email .
- Never log in via a link that is sent by email, but always type the relevant page by hand into the address bar of your browser and log in there. If there are actually announcements of the relevant service, they will be displayed there. In addition, if possible, you should also refrain from carrying out banking transactions via public/third-party WiFi networks , as you never know exactly whether (and in an emergency from whom) these networks are being used be logged.
- Never enter real data in the form fields! Under certain circumstances, the data can even while typing without having to confirm with “continue”.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )