The alleged Telekom email with the threat “Your connection will be blocked” is apparently the new hit among scammer emails.
This email has short but plausible content, which in the end only serves as a transmitter for a Trojan. Interesting: in its presentation, this email follows the tradition of the “lawyer/debt collection/reminder” letters from last year ( compare ), which have not appeared for weeks.
Instead, this email is now on the way, which is also just a Trojan supplier. From an argumentative point of view, this email is similarly cleverly designed, if not better, because it addresses something that not only people are afraid of, but that also affects almost everyone: the blocking of the telecommunications contract!
The particular danger lies in the dynamics of the content, because you are not only addressed with your full name, which can also be found in the file name of the attached .zip file, but the date of the deadline shown is also always plausibly adjusted.
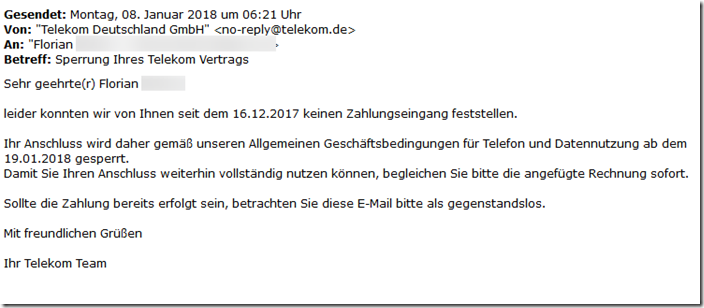
Subject: Blocking your Telekom contract
Dear ***,
unfortunately we have not been able to detect any payment from you since [dynamic date] .
Your connection will therefore be blocked in accordance with our general terms and conditions for telephone and data usage from [dynamic date] .
So that you can continue to fully use your connection, please pay the attached invoice immediately.
If payment has already been made, please consider this email to be irrelevant.
Kind regards,
your Telekom team
The alleged invoice, whose file name also contains the recipient name of the email, immediately appears to be a Trojan.
What is a Trojan?
The way they work is very similar to that of the proverbial Trojan horse : Trojans are programs that appear to be harmless, useful files. In fact, they just disguise themselves as harmless software. In reality, the program causes immense damage to the device.
How can I detect a Trojan?
This is not always easy, because the name of a Trojan identical to a program or data package that is actually harmless to the computer. For example, a Trojan can be called “Microsoft Word 2016” or “Vacation Photos Dominican Republic”. In some cases, however, the file extension can provide information about the true content of the program: Many Trojans are executable .exe files that simulate the installation process of the harmless file, but install spy software or viruses in the background. If a user then notices that executing the file did not install the desired software, but rather that he is led through endless installation processes and ultimately has a lot of new software on the device, but not the one he wanted, this is an indication that to have caught a Trojan.
How can I avoid Trojans?
By carefully checking the source of the file, downloading a Trojan can be avoided. Dubious sites and third-party files often spread Trojans. If possible, programs should be downloaded from the manufacturer's website and not from external service providers. When searching and using pirated software, many files offered do not contain the game or utility, but rather a harmful Trojan. There are also links to clouds or external sites that offer supposedly harmless files and whose harmlessness is not verified by every provider. malware up to a certain size .
How can I protect myself from Trojans?
When unpacking files from an unknown source, anti-virus programs help, as long as the permission settings for them have been set correctly and they ideally check the file before unpacking. Overall, it is highly advisable to use files from known sources to protect yourself from Trojans .
What do I do if my computer already has a Trojan?
Simply uninstalling the Trojan or deleting the file that installed it is not enough. Trojans install keyloggers, backdoor programs and sniffers in the background, which can only be identified and rendered harmless anti-virus software Searching for these manually is almost impossible and leaving the software on the device is more than worrying as sensitive data and passwords can be stolen.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )