Our cooperation partner Trend Micro warns of improved attack methods!
Public cloud services for storing and exchanging files have become an integral part of the lives of many Internet users.
Image source: TrendMicro
But cybercriminals have long since jumped on this bandwagon.
Latest scam: They set up a fake homepage for the popular Google Drive service in order to get users' login details.
Anyone who falls for the trick runs the risk of losing their personal information in the second step.
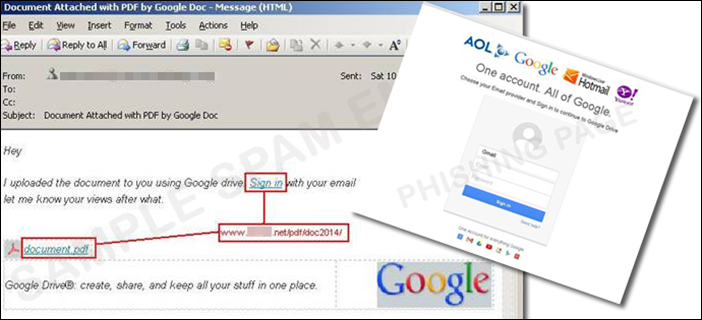
As so often happens, the attack begins with a seemingly harmless email message .
The recipient is directed to a PDF file that can be accessed via Google Drive.
Anyone who clicks on it will be redirected to the fake homepage. After entering the access data, the PDF file opens, which does not contain any malicious code and provides information on financial topics.
Image source: TrendMicro
Anyone who makes a typo or enters imaginary data on the supposed login page will not be able to access the document, as only correct input formats are accepted - which could lead the user to believe that this is really the real Google Drive page. Unfortunately, mobile users are also affected by the attack.
“You can’t repeat it often enough. Users should never click on attachments or web addresses in unsolicited email messages...
...says security expert Udo Schneider, press spokesman for the Japanese IT security company Trend Micro.
“In this case too, the message appears completely harmless. The only difference to the real Google Drive page is that users can log in with other credentials than the Gmail ones that the real Google Drive expects. In this way, cybercriminals can also obtain access data from users who do not even use Google’s email service.”
More information at: Phishers improve system with fake Google Drive sites
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )