The Italian company “Hacking Team” has recently become particularly well known because they themselves fell victim to a hack attack. However, the published data exposes the company's dirty business practices.
First of all: As far as we know, the security gap described in the article was only exploited on Apple devices. Android systems were apparently not attacked
What do you do as a user if a message suddenly appears on your cell phone asking you to download the latest version of, for example, Skype or the Facebook app? Of course you carry out these updates.
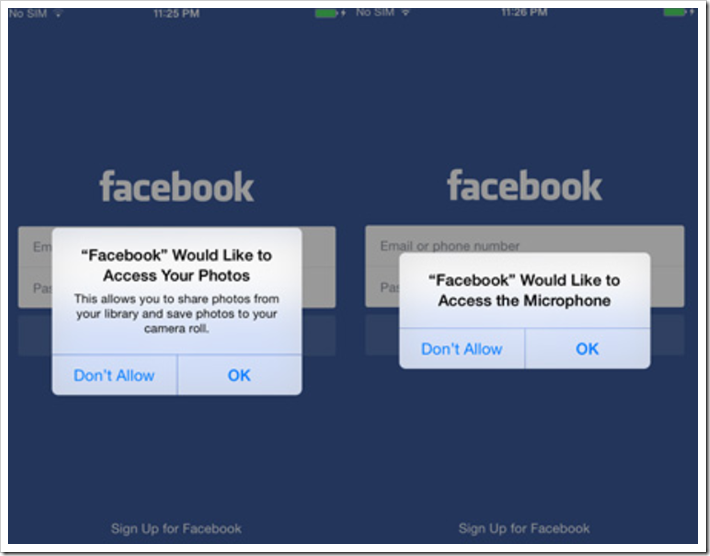
A fake Facebook app obtains permissions (Image: FireEye).
However, documents from the company Hacking Team published by hacken show: The company systematically manipulated users with such fake messages and was thus able to install spyware, i.e. espionage software, on the devices.
Zdnet writes: Popular messengers and social network apps were primarily counterfeited. These included Twitter , Facebook , Facebook Messenger , WeChat , Google Chrome , Viber , Blackberry Messenger , Skype , Telegram and VK . Since the bundle identifiers are identical to those of the originals in Apple's App Store, they can immediately replace the real apps on devices with iOS versions up to 8.1.3 .
The updates could not be distinguished from the normal application and had all their functions. However, it could be used to intercept text messages, voice transmissions and telephone calls. Browser histories could be copied, as could encrypted communication via Whatsapp or other messengers, GPS coordinates or images from the gallery. A wiretapping and espionage scandal of gigantic proportions.
How did the attacks work??
Hacking Team employees took advantage of a loophole called “Masque Attack Apps.” With this gap, which is actually considered to be fixed, fake real apps are installed as updates over the real ones, i.e. a kind of mask that looks like the original but has many more (hidden) permissions.
The data thieves had another trick that also made newer iOs versions vulnerable: They were able to determine the identity of their “update” uniquely for each victim, so that the operating system could not tell whether it was a real or a fake update.
[adrotate group=“1″]
There was also an application called “Newsstand-ipa”. Among other things, this built a virtual keyboard that could read the victim's input and also extracted sensitive data from the cell phone.
What can I do?
The fake apps cannot be recognized by normal users. If you are worried about being affected, first get the latest iOS version , then uninstall all apps if possible and download them again from the App Store. It is important that the apps only come from reputable sources. Third-party sites should be taboo.
Conclusion:
This scandal shows once again how vulnerable cell phones and tablets are to attacks. An up-to-date antivirus software should therefore be mandatory. Because it also warns you about dubious sources for updates.
Author: Lars R., mimikama.org
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )