A particularly insidious form of cybercrime that primarily targets young people is sextortion fraud. Criminals threaten to make victims' intimate images or videos public if their demands for more images, sexual favors or money are not met.
Meta, the company behind platforms like Facebook and Instagram, has taken important steps to address these threats in collaboration with the National Center for Missing & Exploited Children (NCMEC) and Thorn, a nonprofit organization dedicated to protecting children to strengthen young people and their environment.
Expansion of “Take It Down” for global access
“ Take It Down ,” a program designed to combat the distribution of intimate images without consent, is a flagship project in this initiative. Originally only available in English and Spanish, the platform is now expanding to numerous other languages and countries. This enables millions more young people worldwide to be proactive and take back control of their intimate images. The platform is extremely user-friendly to use: young people can generate and submit a unique hash value of their image or video without the sensitive data having to leave their device. Partner companies like Meta can then use this hash value to identify and remove copies of the image on the Internet.
There are several ways to use Take It Down to find and remove intimate images or prevent them from being distributed at all:
- Young people under the age of 18 who are concerned that their content has been or may be posted online
- Parents or trusted adults on behalf of a young person
- Adults concerned about images taken of them when they were under 18.
- “Take It Down” was designed to respect the privacy and data protection of young people. To start the process, teens can http://TakeItDown.NCMEC.org and follow the instructions to assign a unique hash – a digital fingerprint in the form of a numerical code – to their image or video.
- Teens only need to submit the hash, not the intimate image or video itself, which never leaves their device. Once the hash is submitted to NCMEC, companies like Meta can track down copies of the image, remove them, and help prevent future publications by those who threaten to do so.
New resources for teens, parents and teachers
In addition to the technical solution, education and awareness-raising play a crucial role in the fight against sextortion. Meta and Thorn have therefore developed a comprehensive range of information that helps young people, their parents and teachers to recognize sextortion, protect themselves against it and react appropriately if it occurs. These resources are part of the expanded Stop Sextortion portal and include practical tips and contact information for help.
Kelbi Schnabel, Senior Manager at Thorn, said: “ Our collaboration with Meta to provide targeted and robust sextortion resources has significantly strengthened Thorn's efforts in the fight against sextortion. Our joint initiative is already empowering parents and young people to understand the risks and take action, demonstrating the power of collective action in tackling complex challenges like sextortion. The result of our collaboration underscores the importance of accessible and comprehensive resources in the digital age.”
Global campaign to raise awareness
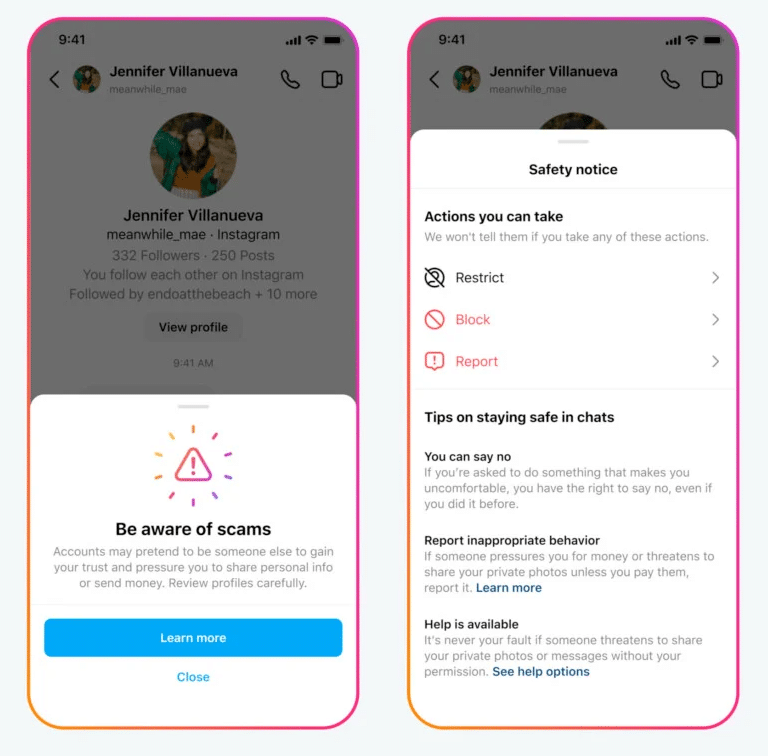
To maximize the reach and effectiveness of these measures, Meta is launching a global campaign involving both safety organizations and creatives to raise awareness of sextortion and spread prevention strategies. Meta also relies on preventative security measures in its apps, such as security warnings for potentially fraudulent contacts and stricter settings to protect the privacy of young people.
Questions and answers about protection against sextortion
Question 1: What is sextortion and how common is it?
Answer 1: Sextortion is a form of blackmail in which perpetrators threaten to publish intimate images or videos in order to extort money, additional images or sexual favors from victims. This form of cybercrime is increasing and primarily affects teenagers and young adults.
Question 2: How does the Take It Down program work?
Answer 2: The Take It Down program allows teens to create and submit a digital fingerprint (hash) of their intimate images without having to upload the image itself. Partner companies like Meta use this hash to find and remove copies of the image on the Internet.
Question 3: How can teenagers, parents and teachers prevent sextortion?
Answer 3: It is important to be informed about the risks, to handle personal data responsibly on the Internet, and to be aware of offers of help. Meta and Thorn provide extensive resources and tips on preventing and responding to sextortion.
Question 4: How does Meta support young people affected by sextortion?
Answer 4: Meta not only offers technical solutions like “Take It Down”, but also educational materials and safety instructions in its apps. Young people are actively informed about protective measures and offers of help.
Question 5: What can the global community do to combat sextortion?
Answer 5: In addition to the use of programs like “Take It Down”, international cooperation between organizations, companies and governments is essential. Joint efforts in education, technology development and law enforcement are necessary to effectively combat sextortion.
Conclusion
Meta's efforts to expand the Take It Down program and create new resources in collaboration with Thorn are critical steps in the fight against sextortion. By providing tools and information that empower youth to protect themselves and promoting global awareness of the dangers of sextortion, these initiatives set new standards in digital youth and data protection. However, it is important that these efforts are complemented by continued education and the development of additional protection mechanisms. Everyone can contribute, whether by raising awareness, supporting affected youth or participating in prevention programs.
Source: Meta
To learn more about these important topics and how you can get involved, sign up for the Mimikama newsletter and find out about our online lectures and workshops .
You might also be interested in:
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )

