Phishing scammers don't sleep! And they are constantly working on the biggest weak point of their scams: the cover letter, or the argument with which they lure the recipients into their traps.
Important note: The company mentioned (PayPal) has nothing to do with the scam . You yourself have become a victim here, with your name being misused to lure users into a trap!
It is always important that the email appears authentic, contains few errors, and ideally no errors at all, and that the argument intended to unsettle the recipient also appears convincing.
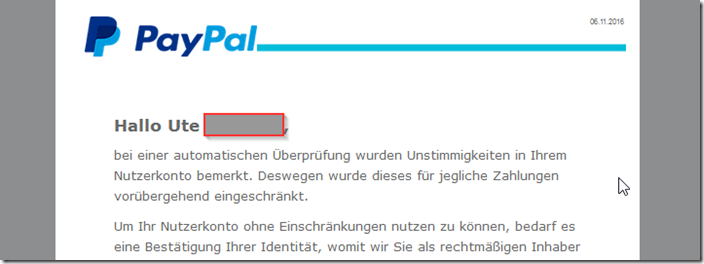
Hello Ute [***],
During an automatic check, discrepancies were noticed in your user account. That is why this has been temporarily restricted for all payments.
In order to be able to use your user account without restrictions, your identity must be confirmed, which we use to authenticate you as the rightful owner.
Simply click HERE
Your user account is freed from all restrictions immediately after your identity has been successfully confirmed.
Kind regards,
PayPal Customer Service, Martin Wagner
In addition to the factor of correct salutation, the graphic structure is always important. This email also uses a fake signature from a customer service employee.
Currently NOT available
During our analysis, the phishing website to which the built-in link under “Continue to confirmation” refers was not accessible ( http://payser.info/ ). Nevertheless, we can observe again and again that phishing emails with strong arguments are repeatedly reused and given a different link. So we assume that this email will appear again and then carry a sharp link.
General phishing warning:
- Phishing emails generally try to appear as if they come from the relevant company . Fraudsters use these to try to get personal data, preferably bank credit cards or other payment data.
- Protection software is helpful! With updated databases and appropriate heuristics, malicious sites are often blocked. We use Kaspersky protection software .
- The real “art” of these emails is the story with which the recipient is supposed to trust the email and open the inserted link. Expression, grammar and spelling, as well as plausibility and individuality play a very important role here. Especially in the recent past, there have been an increasing number of emails that shined with individuality: they could address the recipient with the correct name and also provide actual address and personal data.
- However, you can generally note: Banks, payment and purchase portals never ask you to log in to the account using a built-in link! In addition, although a generic salutation is always an indication of phishing, an existing correct salutation is not proof of the authenticity of an email .
- Tip on your smartphone: press and hold a link until a dialog window opens with the link preview. This shows where an embedded link should lead.
- Never log in via a link that is sent by email, but always type the relevant page by hand into the address bar of your browser and log in there. If there are actually announcements for the relevant service, they will be displayed there. In addition, if possible, you should also refrain from conducting banking transactions via public/third-party Wi-Fi networks , as you never know exactly whether (and in an emergency, by whom) these networks are being logged.
- Never enter real data in the form fields! Under certain circumstances, the data can even while typing without having to confirm with “continue”.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )