In recent days, a worrying wave of phishing attacks on bank customers has hit Germany. Scammers' methods are not new, but their tactics are becoming increasingly sophisticated. The aim of the criminal activities is to obtain sensitive user data via fake emails. The attackers use the names of large German banks to deceive their victims.
Attack on Postbank customers
The fraud attempts often begin with a threat: the customers' accounts will be blocked if action is not taken immediately. The emails, which are sent in the name of Postbank, suggest that the recipient's account will be blocked within the next 24 hours due to alleged security checks. Customers are encouraged to update their online profile to prevent deactivation.

Such threats put recipients under pressure and are intended to encourage them to react hastily and thus reveal personal data.
Deutsche Bank and the “photoTAN process”
A similar scenario is playing out with Deutsche Bank customers. Here, users receive emails asking them to reactivate their “photoTAN procedure” due to an allegedly expired security certificate. The fraudsters set a deadline and threaten to restrict account access, which increases the pressure on the recipients and can lead them to take rash actions.

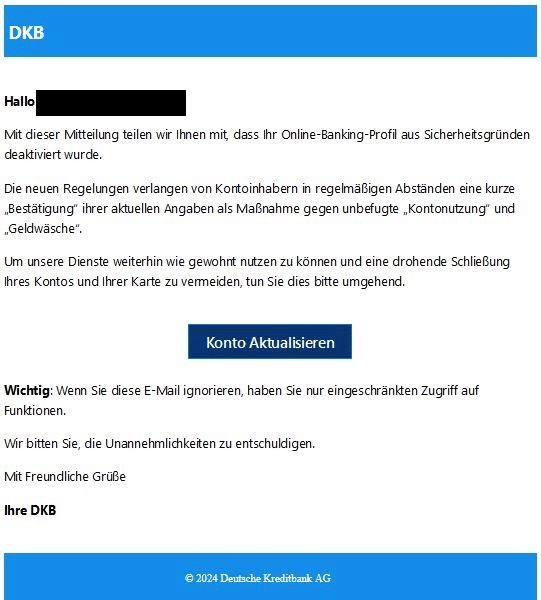
DKB and the fake account blocking
DKB customers are also affected. Phishing emails claim that the online banking profile has been deactivated for security reasons. Customers will be asked to confirm their details to reactivate the account. A personal salutation is often used to create trust and legitimacy.
ING bank and the incorrect registration details
The ING bank is also affected by phishing attacks. Customers receive messages announcing account suspension due to allegedly incorrect login credentials. As in the other cases, an update of personal data is required. What is particularly perfidious here is the indication that the data would be treated securely “according to strict guidelines”, which is intended to give the fraudulent emails a serious appearance.

questions and answers
- How do I recognize a phishing email?
Watch out for impersonal salutations, spelling mistakes, unusual wording and requests to provide personal information via links or forms. Also check the sender address carefully. - What should I do if I receive a suspicious email?
Do not respond to the email, do not click on links and do not provide any personal information. Instead, move the email to the spam folder. - How can I best protect myself from phishing?
Regularly update your software, use comprehensive security software protection, and be particularly vigilant about emails that request you to take action under pressure. - How do banks usually react if there is actually a security problem?
Reputable banks generally will not contact you via email to ask you to perform sensitive actions such as updating security information or entering personal information. - Can I report somewhere that I received a phishing email?
Yes, many banks offer the option of reporting suspicious emails directly to a special address. This helps banks become aware of new fraud methods and warn other customers.
Conclusion
Vigilance against phishing remains an ongoing necessity. Recognizing the signs of a phishing email and responding correctly will not only protect your own data, but will also help reduce the effectiveness of such scams. Stay critical and informed to protect yourself and your digital life.
Source: Consumer Protection
Stay up to date by subscribing to our newsletter and participating in our online lectures and workshops .
You might also be interested in:
Musicians beware: Spam emails promise valuable piano
Expose app traps: Protect your child from hidden costs
Less ransom, more resistance: trend reversal in ransomware
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )

