Ransomware refers to malicious programs that encrypt files on the computer. Criminals then demand a ransom so that the files can be decrypted again (from the English holding ransom = hostage/blackmail). Such traps now also appear on what appear to be porn sites, which quickly disappear and reappear with a new address.
The image trap
The trap can actually only work because the file extensions are hidden in most Windows systems. Windows apparently wants to protect users from accidentally deleting the file extension when renaming a file, but the downside is that this makes it easier for criminals to set up such traps in the first place.
Specifically, when you access pages that have meaningful names like nude-girlss.mywire, it pops. org, sexyphotos. kozow. com or sexy-photo. have a photo online (you don't even need to try, these pages have now been deleted!) that you should download.
But be careful: If the file extension is switched off, it looks as if a .PNG image file is being downloaded, but the file is actually called SexyPhotosJPG.exe, for example, and is therefore an executable file!
After execution you have Ransomware Light
If you are so reckless as to download the “image” and use it to start the file (because it could be that the longed-for stock market report is behind it), the following happens:
- The files del.exe, open.exe, windll.exe, windowss.exe and avtstart.bat are placed in the temporary folder and executed
- The windowss.exe file creates additional files, including a windows.bat that renames
- The windll.exe file creates a readme file that contains further information
The files are just renamed!
Afterwards, several folders on the computer look like this:
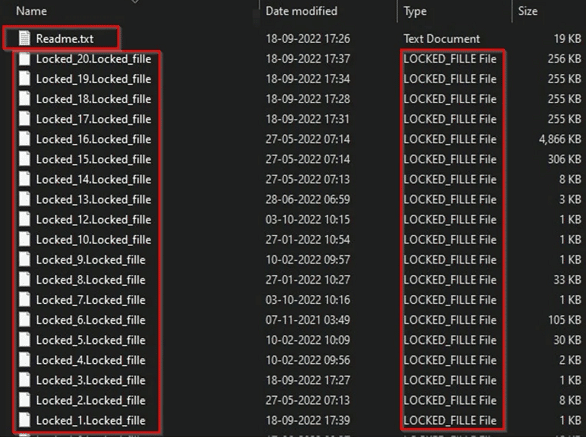
The files then have names like Locked_20.Locked_fille, but are not encrypted , they have just been renamed. With a little effort and trial and error, important files can be restored by hand, although this can be very tedious depending on the number of files.
The “blackmail letter”
Each folder also contains a Readme text file containing further information:
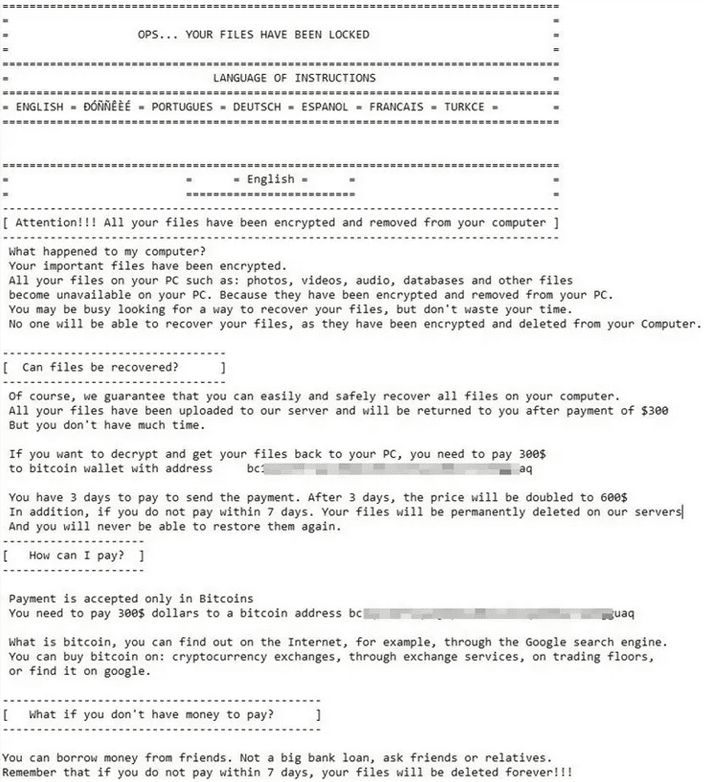
The file states (incorrectly) that the files have been encrypted and that you should pay $300 via Bitcoin within seven days (the ransom doubles to $600 after three days), otherwise the files will be permanently deleted.
However, the files are not sent to any “server” and their original names are not stored anywhere! So even if you pay the ransom, the files will remain renamed!
What can I do if this happened to me?
There are only two options:
- Either try to restore at least the most important files by renaming them by guessing the file extension
- Or restore the operating system to a previous state (system restore)
The second method works well because it is not real ransomware, which would also encrypt so-called “shadow copies”.
So it's better to go to more well-known sites. Or look at the stock market reports. Depending on which is more arousing.
Article image: Unsplash
Sources:
Cyble , Bleeping Computer , PC World
Also interesting: There is currently an email circulating that supposedly comes from a tax advisor.
However, the message is not attached to a tax notice, but rather a Trojan that can infect your computer or smartphone/tablet with malware. – Trojan warning: email with tax notice
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )

