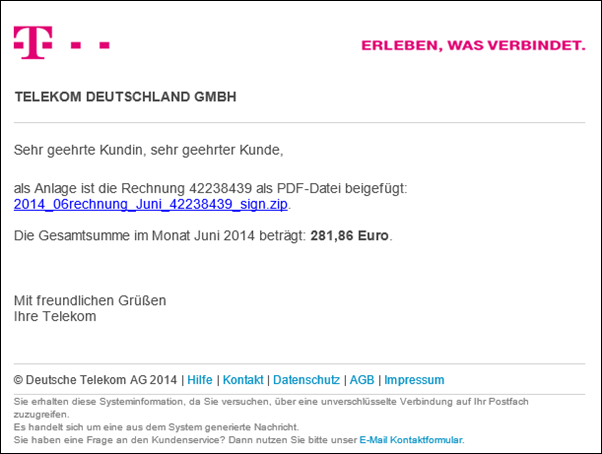
Internet fraudsters send an email in the name of “Telekom”. The user is led to believe that he has an invoice to pay for May or June 2014.
The user can now view the details of the invoice by following a link in the email.
DANGER! Internet fraudsters try to convince users to download an invoice using false facts. But this is not an invoice but a TROJAN!
This is what the fake email looks like:
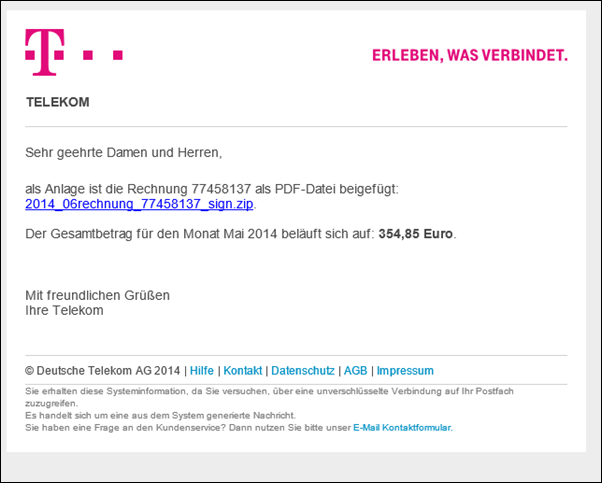
And so those for June 2014
The email in full:
Ladies and Gentlemen
Invoice 77458137 is attached as a PDF file:
2014_06rechnung_77458137_sign.zip.The total amount for the month of May 2014 is: 354.85 euros.
Kind regards, your Telekom
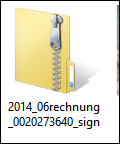
The user follows the instructions and clicks on “2014_06rechnung_77458137_sign.zip. then a file in *.zip format will be downloaded!
ZDDK NOTE: The number of the “booking account” and the outstanding amount may vary. Not every user who receives this email has the same booking number and the same amount in their email!
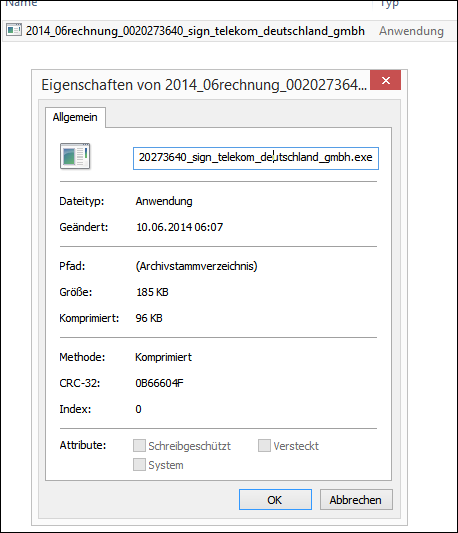
This file contains an *.exe file, i.e. an executable file / application.
What is a TROJAN?
Trojans are standalone programs (.exe) that pretend to be something other than what they really are. In this case it should appear as if it is an invoice from Telekom.
When you run the file, it seems like nothing is happening. But that's not true. A program is installed in the background. The programs or internet fraudsters behind such programs now have access to your data or can also have complete control over your computer.
Fell into the trap?
1) Anyone who opens or has opened the file attachment should first have their PC scanned by their current antivirus program .
If this does not lead to any result, you can also use a “ system restore ”.
2) Change all passwords to social networks, online shops, etc. Also inform your bank (online banking) and / or your credit card company.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )