Users are currently being misled by internet fraudsters via email with different senders such as “WhatsApp, voice mail report” or “Telekom, sending voice messages”. The subject says: “You have received a voice mail” – or “A voice message has been left for you”
These are the emails we're talking about at the moment:
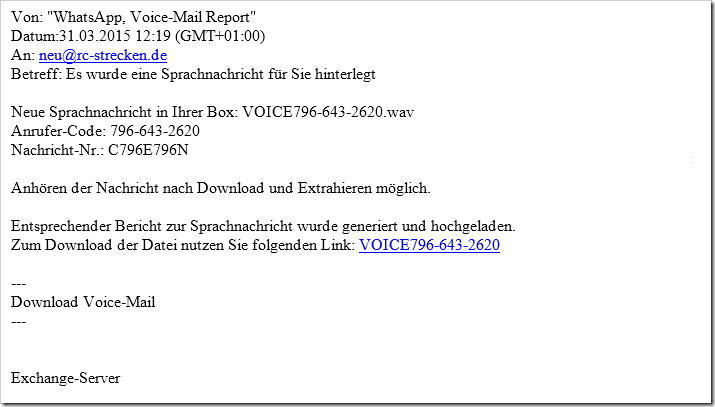
From: “WhatsApp, Voice-Mail Report”
Date: March 31, 2015 12:19 (GMT+01:00)
To: ~~~~~~~~~~~~
Subject: A voice message has been left for youNew voice message in your box: VOICE796-643-2620.wav
Caller Code: 796-643-2620
Message No.: C796E796NListening to the message is possible after downloading and extracting.
Corresponding voice message report has been generated and uploaded.
To download the file, use the following link: VOICE796-643-2620
—
Download Voice Mail
—
Exchange Server
—
The emails can also contain the following content:
From: “Telekom, sending voice messages”
To: ~~~~~~~~~~~
Date: March 31, 2015 at 12:41
Subject: You have received a voice mailYou have a new voice message: VOICE587-566-3638.wav
ID no.
Caller: 587-566-3638 Message ID: C66P66BYou can listen to the file after downloading and unpacking it.
Voice message report has been uploaded.
You can access your message using the following link: VOICE587-566-36385 (WAVE Audio File Format).
—
Make voice messages available
—
Server data exchange
—
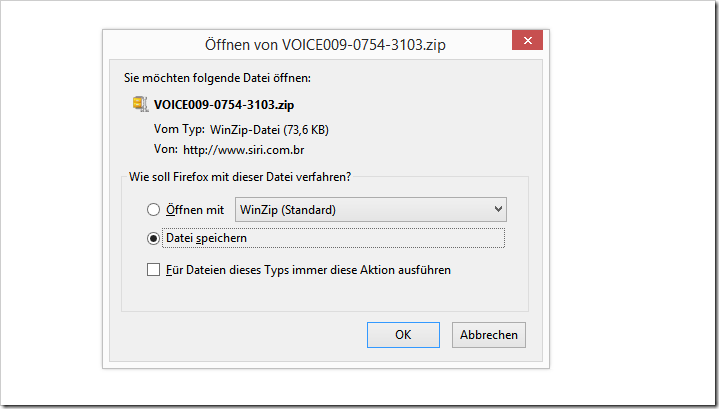
If a user clicks the link/note in the email, their web browser opens and an attempt is made to save a ZIP file to the computer.
It looks like this:
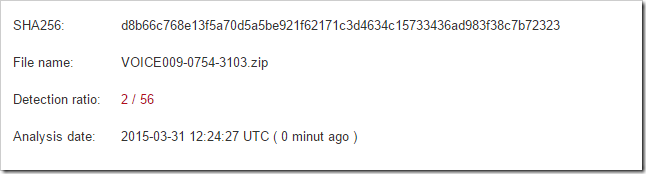
However, this file does not contain a voice message - but a Trojan! We have had this file checked.
At the moment (March 31, 2015 / 2:25 p.m.) only 2 of a total of 56 antivirus software manufacturers recognize the Trojan:
What is a TROJAN?
Trojans are standalone programs (.exe) that pretend to be something other than what they really are.
When you run the file, it seems like nothing is happening.
But that's not true! A program is installed in the background. The programs or internet fraudsters behind such programs now have access to your data or can also have complete control over your computer.
Fell into the trap?
1) Anyone who opens or has opened the file attachment should first have their PC scanned by their current antivirus program .
If this does not lead to any result, you can also use a “ system restore ”.
2) Change all passwords to social networks, online shops, etc.
Also inform your bank (online banking) and/or your credit card company.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )