The current wave of phishing is quite dangerous: there are hardly any weaknesses and the consistent use of the recipient's full name in the salutation creates a false authenticity.
Important note: The company mentioned (PayPal) has nothing to do with the scam . You yourself have become a victim here, with your name being misused to lure users into a trap!
This email is also tough again. However, the following content is fake:
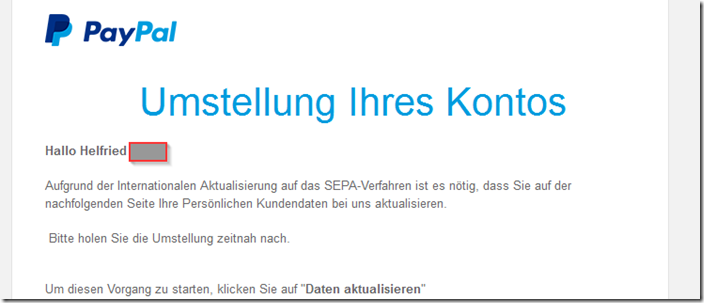
Conversion of your account
Hello Helfried [***],
Due to the international update to the SEPA procedure, it is necessary that you update your personal customer data with us on the following page.
Please make the change as soon as possible.
To start this process, click on “ Update data “
Why is this necessary?
Since 2016, the new IBAN has been in effect for payments within Germany instead of the account number and sort code - it regulates all bank transactions within the EU and Switzerland.
The content is of course fictional. An update of existing data is NOT necessary. The aim of this email is to unsettle the recipients and respond to this warning by clicking on the built-in link to update the data.
Phish
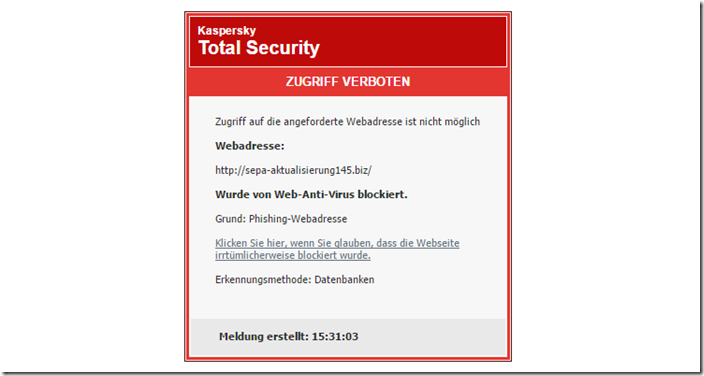
Stop! This is phishing and there is a trap behind this link. Our Kaspersky protection software warns directly about a phishing web address.
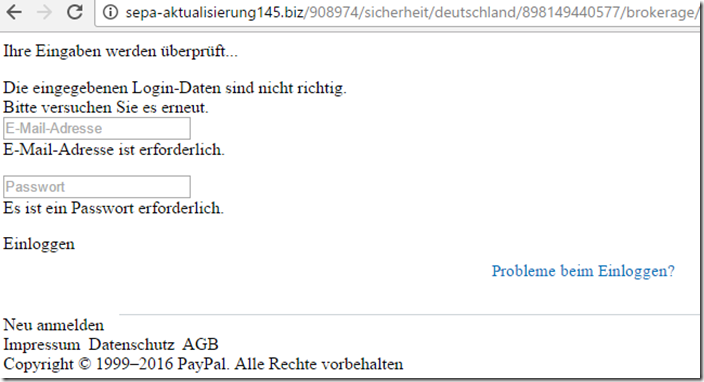
At the address “sepa-aktualisierung145.biz” you are directed to a fake website. In contrast to the email, however, the website is currently in a faulty state: the graphics are not displayed and therefore the fraud process was ultimately easy to understand at the time of our analysis.
However, we must warn: this incorrect situation can be remedied at any time! The same applies here: please do not enter any valid data into these login fields, as these will end up directly in the hands of unknown fraudsters.
General phishing warning:
- Phishing emails generally try to appear as if they come from the relevant company . Fraudsters use these to try to get personal data, preferably bank credit cards or other payment data.
- Protection software is helpful! With updated databases and appropriate heuristics, malicious sites are often blocked. We use Kaspersky protection software .
- The real “art” of these emails is the story with which the recipient is supposed to trust the email and open the inserted link. Expression, grammar and spelling, as well as plausibility and individuality play a very important role here. Especially in the recent past, there have been an increasing number of emails that shined with individuality: they could address the recipient with the correct name and also provide actual address and personal data.
- However, you can generally note: Banks, payment and purchase portals never ask you to log in to the account using a built-in link! In addition, although a generic salutation is always an indication of phishing, an existing correct salutation is not proof of the authenticity of an email .
- Tip on your smartphone: press and hold a link until a dialog window opens with the link preview. This shows where an embedded link should lead.
- Never log in via a link that is sent by email, but always type the relevant page by hand into the address bar of your browser and log in there. If there are actually announcements of the relevant service, they will be displayed there. In addition, if possible, you should also refrain from carrying out banking transactions via public/third-party WiFi networks , as you never know exactly whether (and in an emergency from whom) these networks are being used be logged.
- Never enter real data in the form fields! Under certain circumstances, the data can even while typing without having to confirm with “continue”.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )