Beware of alleged ING Diba emails that claim to be an information letter about a new tanning procedure! These emails are attempts at fraud with the aim of obtaining sensitive banking information.
In this case it is a very carefully thought out and clearly structured email that comes without any linguistic barriers and for this reason represents a particular danger. In addition, the recipients of these emails are addressed by their real names.
The content of this email is in accessible plain text:
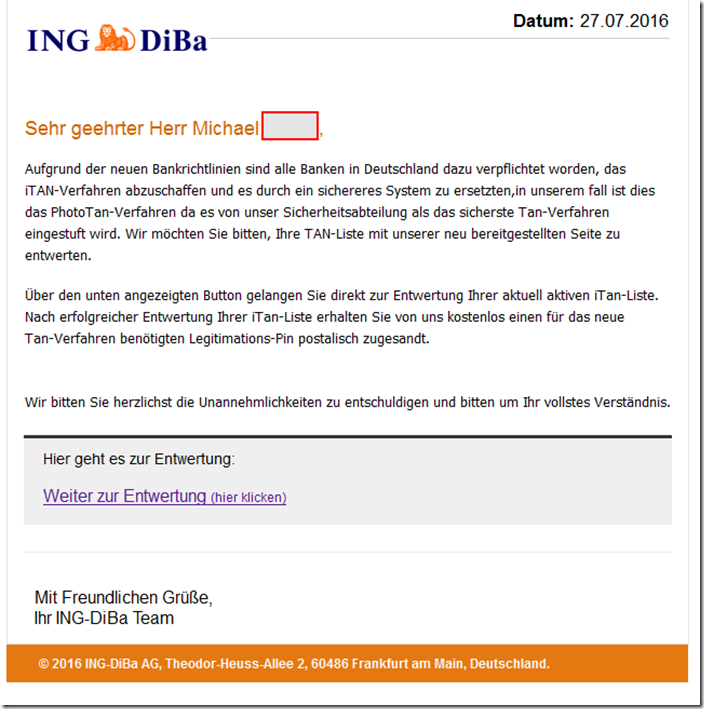
Dear Mr. Michael [***],
Due to the new banking guidelines, all banks in Germany have been obliged to abolish the iTAN procedure and replace it with a more secure system, in our case this is the PhotoTan procedure as it is classified as the safest tan procedure by our security department. We would like to ask you to invalidate your TAN list using our newly provided page.
The button shown below will take you directly to the cancellation of your currently active iTan list. After your iTan list has been successfully validated, we will send you the identification pin required for the new Tan process by post free of charge.
We sincerely apologize for the inconvenience and ask for your full understanding.
Click here for validation:
Continue to validation (click here)
Kind regards,
your ING-DiBa team
The aim of this email is of course to irritate the recipient and manipulate them into clicking on the link behind “ Continue to cancellation (click here)” .
Phishing scam
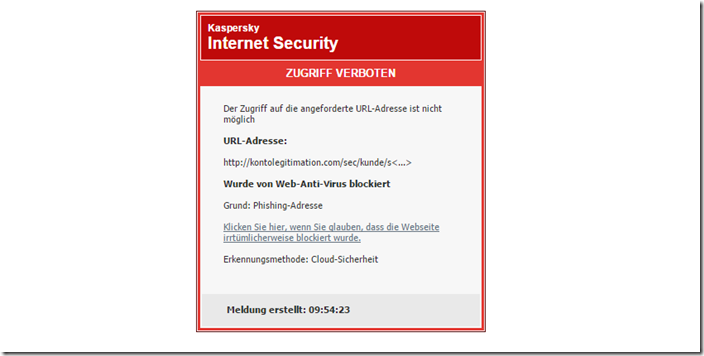
However, this email is a phishing scam, the sender is of course not ING DiBa, and there is no change to the TAN procedure. Our phishing protection from Kaspersky Internet Security blocks the dangerous website directly even after clicking on the built-in link.
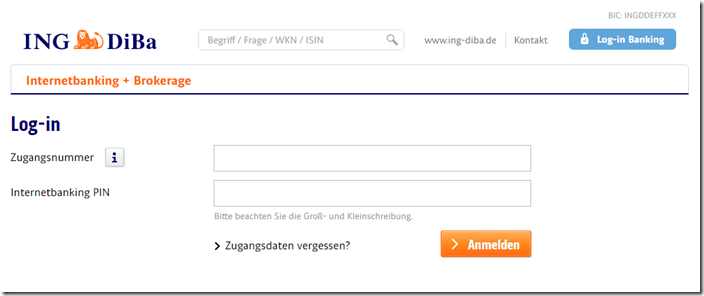
Without phishing protection, a page that is modeled on ING DiBa opens, but is a fake from the hands of fraudsters. In the address bar there is a page with the address “kontolegitimation.com” . You can see that even the selection of the fake page address was well thought out.
There are several fake form fields here:
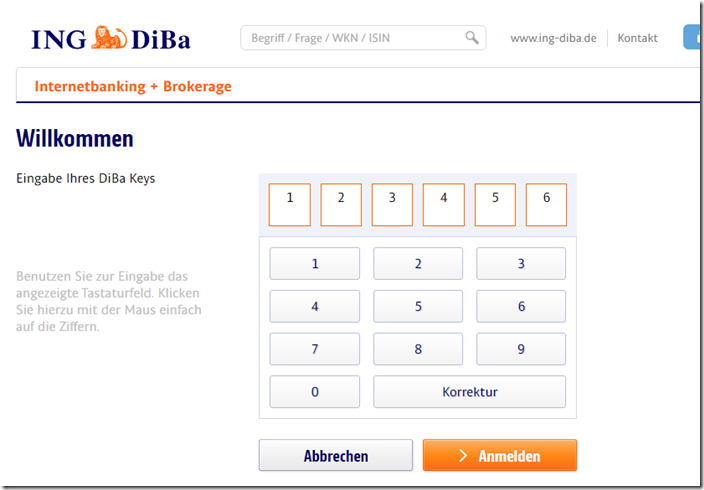
Entering a DiBa key via a virtual click area is a rare element and also underlines how clean this fraud attempt has been so far.
Following this entry, personal data and also sensitive bank details will be requested. Caution! Every type of entry made here ends up in fraudster databases!
General phishing warning:
- Phishing emails generally try to appear as if they come from the relevant company . Fraudsters use these to try to get personal data, preferably bank credit cards or other payment data.
- Protection software is helpful! With updated databases and appropriate heuristics, malicious sites are often blocked. We use Kaspersky protection software .
- The real “art” of these emails is the story with which the recipient is supposed to trust the email and open the inserted link. Expression, grammar and spelling, as well as plausibility and individuality play a very important role here. Especially in the recent past, there have been an increasing number of emails that shined with individuality: they could address the recipient with the correct name and also provide actual address and personal data.
- However, you can generally note: Banks, payment and purchase portals never ask you to log in to the account using a built-in link! In addition, although a generic salutation is always an indication of phishing, an existing correct salutation is not proof of the authenticity of an email .
- Tip on your smartphone: press and hold a link until a dialog window opens with the link preview. This shows where an embedded link should lead.
- Never log in via a link that is sent by email, but always type the relevant page by hand into the address bar of your browser and log in there. If there are actually announcements of the relevant service, they will be displayed there. In addition, if possible, you should also refrain from carrying out banking transactions via public/third-party WiFi networks , as you never know exactly whether (and in an emergency from whom) these networks are being used be logged.
- Never enter real data in the form fields! Under certain circumstances, the data can even while typing without having to confirm with “continue”.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )