The following email, which claims to be Amazon and points out a temporary restriction, is an attempted scam!
The email includes the recipient's address in its subject and also in the text. Seems a little out of place and therefore (and also due to incorrect punctuation and spelling) makes this email quite transparent:
The content of this email is in plain text:
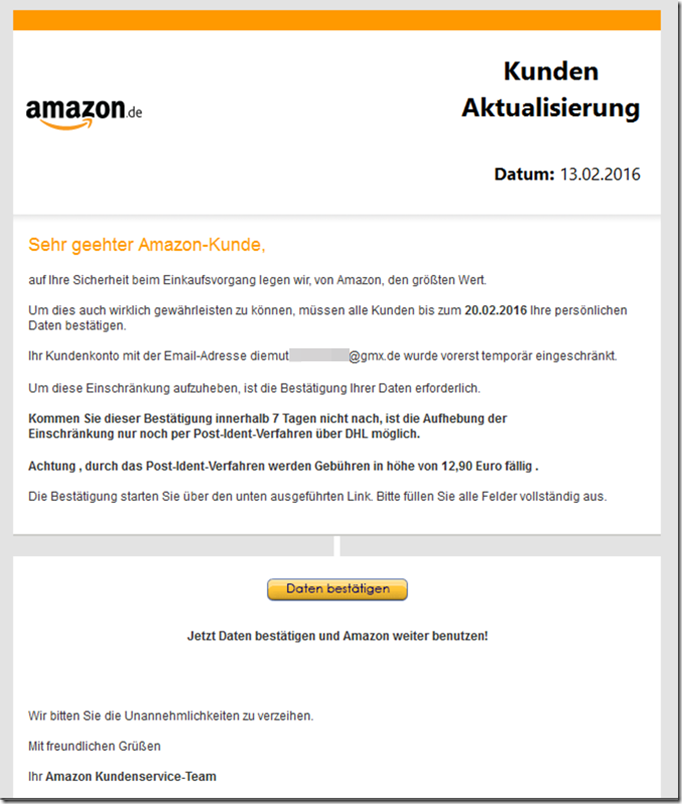
Dear Amazon customer,
At Amazon, we attach great importance to your safety during the shopping process.
confirm their personal data
by February 20, 2016 Your customer account with the email address [email protected] has been temporarily restricted.In order to remove this restriction, confirmation of your data is required.
If you do not receive this confirmation within 7 days, the restriction can only be lifted using the Post-Ident procedure via DHL.Attention, the Post-Ident procedure incurs fees of 12.90 euros.
You can start the confirmation via the link below. Please fill out every field completely.
Of course, the arguments presented are fictitious, they only serve to persuade the recipient of the email to click on your built-in link.
Phish
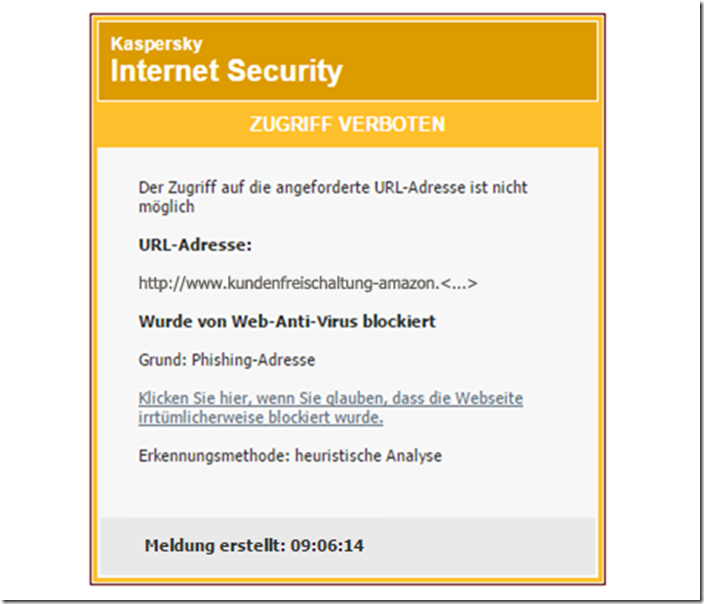
with the help of updated protection software , you will receive a warning immediately after clicking that this is phishing:
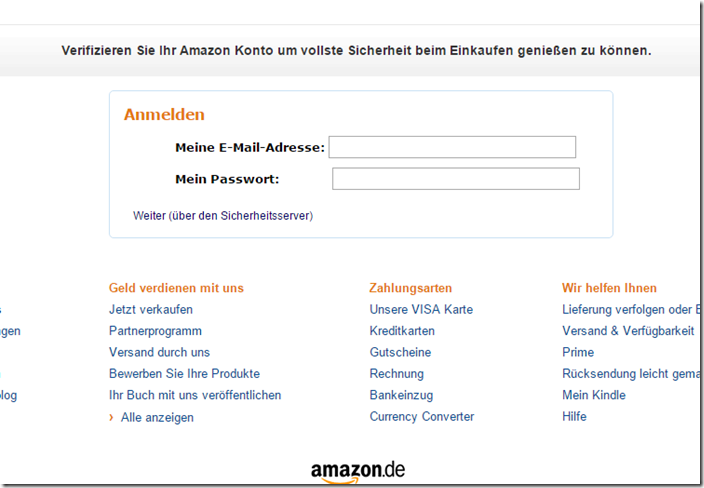
Without protective mechanisms, you end up on a reception page that is modeled on the Amazon login. The site is located at the server address “ kundenfreischaltung-amazon.de ”. Interesting aspect: a .de domain is used here for the attempted fraud.
The “.de” domain
Until now, the country code .de has always been considered quite trustworthy, but this misconception is now being exploited mercilessly. We therefore warn in plain text about the address kundenfreischaltung-amazon.de . We strongly suspect that false information was provided behind this address.
The further process
First, the login details are requested. Anyone who provides correct information here will lose their access data to fraudsters!
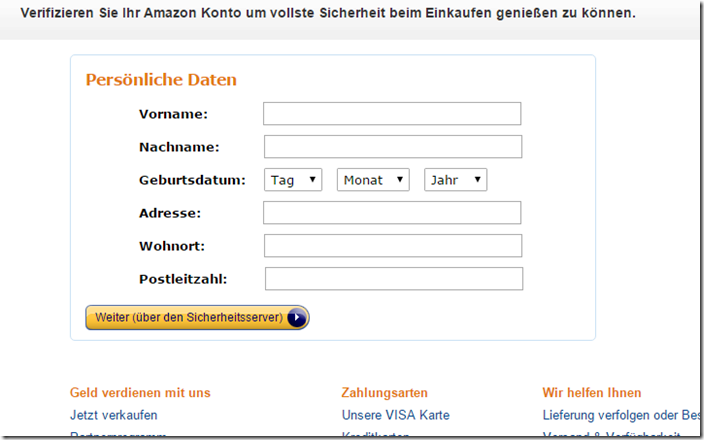
Afterwards, pages open that query personal data, but also sensitive bank data.
Of course, this is a trap - the data provided ends up directly in a fraudster database. An attempt is also made to lull the visitor into security with an authentic-sounding email. The fields shown are now intended to entice you to enter your own data, which, however, ends up directly in a fraudster database.
General phishing warning:
- Phishing emails generally try to appear as if they come from the relevant company . Fraudsters use these to try to get personal data, preferably bank credit cards or other payment data.
- The real “art” of these emails is the story with which the recipient is supposed to trust the email and open the inserted link. Expression, grammar and spelling, as well as plausibility and individuality play a very important role here. Especially in the recent past, there have been an increasing number of emails that shined with individuality: they could address the recipient with the correct name and also provide actual address and personal data.
- However, you can generally note: Banks, payment and purchase portals never ask you to log in to the account using a built-in link! In addition, although a generic salutation is always an indication of phishing, an existing correct salutation is not proof of the authenticity of an email .
- Never log in via a link that is sent by email, but always type the relevant page by hand into the address bar of your browser and log in there. If there are actually announcements of the relevant service, they will be displayed there. In addition, if possible, you should also refrain from carrying out banking transactions via public/third-party WiFi networks , as you never know exactly whether (and in an emergency from whom) these networks are being used be logged.
- Never enter real data in the form fields! Under certain circumstances, the data can even while typing without having to confirm with “continue”.
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )