This finding is surprising: it is generally assumed that the programmers of malicious software are hidden somewhere abroad, where they cannot be legally traced. But now the Microsoft security team discovered an Austria-based company with offices in Vienna and Liechtenstein as the source of a widespread malware called Subzero.
The company
HERE , the company, headquartered in Vienna, has 20 years of experience and develops “ techniques for the collection and analysis of information ”. Among other things, risk analysis processes are offered that “ provide a deep understanding of people and companies and reveal the hidden connections between them ”.
It gets a little clearer here: “ Whether your company needs information about a customer, a competitor, or a potential partner, DSIRF can analyze income sources, understand personal and professional networks, and identify insider and outsider threats .”
These are areas of activity in which legal consultants also operate, but curiously they also describe information that can be obtained through the use of malware and spyware on a customer or competitor - spy software that was used by the company as early as November 2021 (see HERE ). made headlines.
The malware is being actively used
In December 2021, “Netzpolitik” (see HERE ) obtained a company presentation from the company in which the Subzero malware was presented as a “state-of-the-art computer surveillance tool” that could be used to combat terrorism, crime and financial fraud - in other words as “State Trojan”.
However, what was theoretical just a few months ago has now been confirmed by Microsoft: the Subzero malware will be distributed in 2021 and 2022 via a variety of methods, to banks, law firms and companies that have proven unwilling to participate in verification tests their security concepts, meaning it was unauthorized, malicious activity.
Victims observed so far include law firms, banks and strategic consulting firms in countries such as Austria, the United Kingdom and Panama.
How Subzero infiltrates
The Microsoft security team discovered in May 2022 that Subzero was packaged into PDF documents that were emailed to victims. A vulnerability in Windows (patched in July) was also exploited, which is very insidious: the malware was able to write a malicious DLL to the system directory, even if the actual programs were running in a secured system (“sandbox”).
However, employees of companies that only have limited rights to their Windows computers are on the safe side: writing this malicious DLL only worked if they also have the corresponding rights on the PC - and in companies these are usually only given to administrators.
In 2021, Subzero also exploited security holes in Windows that have since been closed. Curious: The malicious DLL that was used at the time even openly contains the signature of the above-mentioned company:
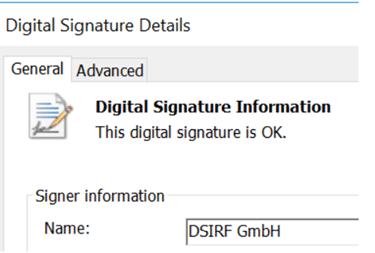
also discovered in Excel documents that appeared to come from real estate companies. But Subzero used another special method: part of the code was packaged in an image!
Now image files alone are not dangerous, but Subzero does the following: The malware also installs a downloader that downloads additional data from the Internet, including this image (don't worry, it is NOT infected!):

The image is loaded into the %TEMP% directory and is not recognized as malicious. Why is that? It's just a picture. However, in the last lines of the image's program code there is hidden part of the malware, which is decrypted and installed by the already installed malware.
Measures against the malware
Microsoft is currently continuously monitoring the malware's actions; the Windows operating system and Office programs have already been patched against Subzero. Users should keep Windows, Office products and Adobe Reader up to date.
If Subzero is already on the computer, Microsoft Defender Antivirus will detect it with the following names:
- Backdoor:O97M/JumplumpDropper
- Trojan:Win32/Jumplump
- Trojan:Win32/Corelump
- HackTool:Win32/Mexlib
- Trojan:Win32/Medcerc
- Behavior:Win32/SuspModuleLoad
In this case, the computer should be thoroughly cleaned with anti-malware programs, as Subzero allows extensive control of the computer.
Article image: Pixabay
Source: Microsoft
Also interesting:
The Google Playstore is generally considered relatively safe, but criminals still managed to infiltrate over 50 apps contaminated with malware, which were downloaded over 300,000 times.
– Over 50 apps in the Google Playstore contaminated with malware!
Notes:
1) This content reflects the current state of affairs at the time of publication. The reproduction of individual images, screenshots, embeds or video sequences serves to discuss the topic. 2) Individual contributions were created through the use of machine assistance and were carefully checked by the Mimikama editorial team before publication. ( Reason )

